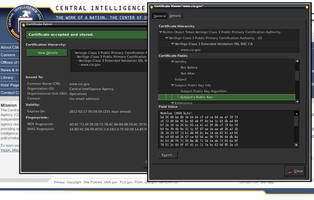
You'll see certificate information pop up whenever you visit a
new https: website, including https://addons.mozilla.org for
example. "New" is anything Patrol hasn't seen and stored yet.
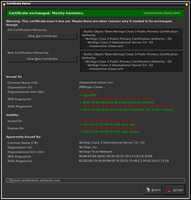
You are also prompted whenever a web site updates its certificate
and given the opportunity to compare the two certificates side by
side, line by line. See the screenshot for an example.
Even if you do not fully understand what is shown to you, you
get a chance of distinguishing legitimate from suspicious changes.
Here's a little list of things to look out for:
- If the old certificate is about to expire (Validity / Expires On),
it was necessary to replace it with a new one. CertPatrol
will check this for you. - In most cases web sites keep using the same certification
authority (Issued By) over time. Should the web site have changed
its certification authority, make sure the old certificate was
about to expire. CertPatrol will assist you with this. - You may want to consider the most popular CAs (like maybe CAcert, Entrust,
Equifax, GoDaddy, NetworkSolutions, Thawte and VeriSign.. to mention some)
to be less likely to help in MITM attacks, but that is only a guess.
Especially since in each country local CAs may be legitimately
well established. - Comodo, GeoTrust, GlobalSign, QuoVadis, RSA WebTrust and StartCom
are known to offer intermediate CA for money. Still StartCom is extremely
popular with small and private web sites for its free services. - If all certificates you see are always issued by the same
certification authority, you should be very suspicious. Try
searching for random https: sites and see if they still all seem
signed by the same CA. - In case of doubt install the Perspectives or Convergence add-ons to make further checks on the credibility of a certificate. The downside of these add-ons is, you reveal who you communicate with to an external service — so better only use it when necessary. In theory you could have some tech savvy friends run notaries for you, the more the better, but would you want to expose your surfing habits to them?
- If the web site is important to you, make a research on the name of
the new CA. Make a phone call to the owner of the web site and ask them
to confirm the SHA1 fingerprint shown on your screen.
The fingerprint is currently close to impossible to falsify.
Ask them to send you future certificate fingerprints by snail mail
before they install it. - Some clustered sites such as bookryanair.com make things
more complicated by using several inconsistent certificates for the same
domain name. That will look unnecessarily suspicious. Usually such
certificates will look very similar to each other and appear to be
changing frequently. We can only hope for these companies to fix
their set-ups.
It is very important to understand that certificates do not make a statement about the trustworthiness of a web site, but whether that web site is indeed what you think it is. In practice you should always be very suspicious if there are problems with your electronic banking or other sites you trust for very important operations, whereas you can probably relax if a certification problem arises for a web site that you are merely intending to have a quick look at.
The more a web site is important to YOU, the more you should be cautious! That is the most essential rule of thumb in dealing with the wild west of Internet certification today.
This extension is similar to the as yet unreleased 'Certlock'. More info on
http://patrol.psyced.org.
![[Warning]](https://addons.thunderbird.net/static/img/developers/test-warning.png?b=58a99cbb-667a0970) Permissions
Permissions